Stay ahead of the curve with the latest news, ideas and resources on all things Identity Assurance and Passwordless.
Which Form of Authentication Is the Strongest?



Authentication attacks aiming to defraud, steal data or upload malware are among the most common cyberattacks. One of the biggest reasons for this popularity is the relative weakness of many forms of authentication, especially compared to other cybersecurity defense areas.
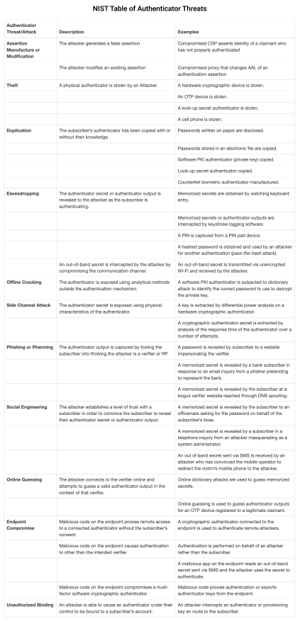
For example, it’s much easier to socially engineer or guess an employee’s login than it is to breach a company’s logical defenses and decrypt what’s stolen. There are several ways attackers can break through authentication systems, and the National Institute of Standards and Technology (NIST) 800-63B outlines the most significant threats, including:
- Theft
- Duplication
- Eavesdropping
- Offline Cracking
- Side-Channel Attacks
- Phishing or Pharming
- Social Engineering
- Online Guessing
- Endpoint Compromise
Below is NIST’s full table of threats to authenticators, along with some examples.
With the large breadth of attack vectors and an increasingly sophisticated cadre of attackers, securing your authentication is essential for keeping your employees, customers and data safe. But which form of authentication is the strongest? In this blog, we’ll rank the strongest authentication forms and the major features and vulnerabilities of each, starting with the weakest.
Which Form of Authentication is the Strongest: Ranked
6. Static Passwords
Security Offered: Low

Features and Vulnerabilities: When debating which form of authentication is the strongest, static passwords fare the worst. Static passwords are vulnerable to virtually all threats, including the simplest forms, such as duplication, theft and online guessing. There are 15 billion stolen passwords readily available on the dark web. They can also be stolen via phishing pages, man-in-the-middle (MitM) attacks and numerous other methods specifically created to get users’ passwords. Hashing offers little protection as most hashed passwords can be cracked fairly easily.
5. SMS 2FA
Security Offered: Low

Features and Vulnerabilities: SMS 2FA is a basic type of multi-factor authentication (MFA) where a user receives a special code, PIN or link or sent to their phone by SMS. This code is intended to prove the user possesses the phone number associated with the account and is referred to as a one-time password (OTP) or time-based OTP (TOTP). It’s a step up from static passwords, but SMS 2FA is not a frontrunner in terms of which form of authentication is the strongest. Though it’s difficult to guess a TOTP before it expires, OTPs can generally be cracked in many other ways. These include eavesdropping using malware or MitM attacks, targeted SMS phishing (smishing), theft through SIM-swapping and social engineering.
4. Phone-as-a-Token MFA
Security Offered: Medium

Features and Vulnerabilities: This authentication method leverages a user’s smart device to prove the MFA possession factor. It’s used as a replacement for hardware tokens as they can be cost-prohibitive to expand to an entire workforce. While phone-as-a-token can deliver a reasonable level of authentication security, this depends on the type of implementation. Systems using OTPs are vulnerable to the same issues as SMS 2FA, while hackers can circumvent push acceptance through social engineering or user fatigue. Theft is naturally an issue as the system is only as secure as the device itself, and a lost device can open up an entire network for an attacker.
3. Hard Token 2FA
Security Offered: High

Features and Vulnerabilities: As ratings go for which form of authentication is the strongest, deploying a hardware (or “hard”) security token as part of a 2FA process is the best password-based option. It counteracts duplication, online guessing and some phishing attacks, though it’s still vulnerable to targeted side-channel, targeted phishing using tools such as Modlishka and social engineering attacks. Another problem facing hard token 2FA is the expense of deploying the tokens, especially for larger enterprises. The system also requires extensive ongoing maintenance to update revocation lists and maintain security integrity.
2. Smart Cards (PKI)
Security Offered: Very High

Features and Vulnerabilities: A smart card authentication system uses card readers attached to PCs to integrate users into a public key infrastructure (PKI). The user’s identity is linked to an X.509 certificate underpinning the private keys on the card. The card securely thus authenticates them and whatever functions they wish to perform inside the enterprise network. In terms of threats, this system effectively protects against duplication, offline cracking and online guessing. Because shared secrets are not used, they also can’t be cracked by phishing or endpoint compromise. However, if a card is stolen in a targeted theft, it’s only as safe as the PIN protecting it, which can be intercepted by eavesdropping.
1. True Passwordless™ MFA
Security Offered: Highest

Features and Vulnerabilities: Although PKI-backed smart cards can be considered secure, the strongest form of authentication is a flexible fully passwordless system based on FIDO standards. This type of solution, termed True Passwordless™ MFA, completely eliminates shared passwords from the process and is tied to the user, not the device. Removing passwords removes the biggest vulnerability and effectively stops attacks such as phishing, online guessing, and social engineering, which comprise the majority of attacks. In addition, since the private keys used for passwordless authentication never leave the secure hardware store where they are held, they are not vulnerable to endpoint compromise. Only in extreme circumstances (if the attacker has access to the silicone on the chip) are they vulnerable to eavesdropping or duplication.
Go Passwordless Today
It’s clear which form of authentication is the strongest when one understands where and how attackers target authentication. As passwords are the most vulnerable and most attacked element in authentication, any secure system must first seek to eliminate them. Naturally, enterprises will have further considerations about which system to deploy, such as user experience and cost of implementation.
HYPR’s passwordless MFA solution is not only the most secure solution, but one that eliminates user friction from the login process so your organization doesn’t have to compromise between security assurance and user experience. HYPR is FIDO Certified from end to end and easily integrates with all major IdPs and SSO providers.
To find out more about how HYPR measures up against other systems in protecting your staff, data and reputation, download our Authentication Attack Matrix. To learn more about passwordless authentication in general, get the Passwordless Security 101 guide.
Joshua Gonzales
Senior Product Marketing Manager
Joshua Gonzales is a Senior Product Marketing Manager at HYPR, where he helps position the company’s authentication solutions in the identity security space. He previously led go-to-market strategies at cybersecurity companies such as Beyond Identity, and also worked as a social media consultant for major brands including HarperCollins and Express. Joshua’s background in cybersecurity and digital storytelling helps convey the importance of eliminating passwords and building trust in the identity lifecycle.
Related Content