Stay ahead of the curve with the latest news, ideas and resources on all things Identity Assurance and Passwordless.
Why You Need to Reconsider OTP Authentication



As part of the general security shift to multi-factor authentication (MFA), one-time passwords (OTPs) have become a common protocol that fulfills the “something you have” requirement of MFA. OTP authentication is fairly easy for organizations to integrate into their authentication strategies and upfront costs are low since most methods leverage users’ existing mobile devices. However, businesses can pay heavily for this expedient choice down the line.
So, what is OTP authentication, how does it work, and what are its limitation? Read on to learn how OTP authentication is defined and how it impacts your organization’s security.
What is OTP Authentication? The Basics
OTP authentication relies on OTPs or time-based one-time passwords (TOTPs), which are unique passcodes that can only be used for a single login instance. The next time a user wants to access an application or website, they will need a different OTP.
So how does OTP authentication work? OTPs are usually generated with algorithms that make use of randomness. This makes it difficult for attackers to successfully guess and use them, unlike traditional passwords. Moreover, since they are used once only, people cannot reuse them across multiple accounts. This OTP security tactic reduces the risk from credential stuffing attacks that use breached passwords from other accounts.
Most OTP authentication involves a code or push notification being sent to a user after they enter their login details. In theory, as the user presumably controls the device or number linked to the account, this process prevents unauthorized account access.
What is OTP Authentication? Examples
SMS and email: The most common example of OTP authentication is a code sent by SMS or email. After a user enters their username and correct password, an OTP is sent to the email or mobile number connected to the account. The user enters this code where prompted to complete the authentication process.
Authenticator apps: One-time passwords can also be delivered directly through smartphone apps as a push notification. This could be a dedicated authentication app such as Google Authenticator, or integrated into the service provider’s app, for example a banking app.
Voice Message: An alternative OTP delivery method is by a voice call on the user’s mobile device. This enables OTP authentication for users with limited sight. The spoken OTP security password is not stored on the user's phone. Voice is also sometimes used as a back-up in case an SMS is not delivered.
The Problems with OTP Authentication
While OTP authentication adds a basic layer of security to password-only defenses, it still can be compromised fairly easily. Today there are even simple kits for purchase that steal OTP security codes for the attacker’s chosen targets using an automated bot service.
Given its vulnerability, authentication standards set by the FFIEC, the OMB’s guidance on the Executive Order on Cybersecurity, and other security guidelines specifically prohibit the use of OTP authentication for proving identity as part of MFA protocols.
There are a number of attacks that expose the vulnerabilities of OTP authentication, especially OTP via SMS, and allow attackers to access accounts. These include:
- SIM-Swapping
- Man-in-the-Middle Attacks
- Brute Force Attacks
- Phishing
SIM-Swapping
SIM-swapping involves criminals using personal information they’ve harvested through social engineering or other methods to persuade the victim’s cell phone provider into switching the number to a SIM card they're in possession of. This gives them access to any OTP authentication codes sent during a login attempt.
Man-in-the-Middle Attack
A man-in-the-middle (MitM) attack is when attackers intercept communications between a server and a device. This can happen through compromised networks or, especially for SMS OTP authentication attacks, through SS7 attacks.SS7 attacks exploit vulnerabilities in the protocol that enables communication between two different mobile network providers to eavesdrop on a particular user.
Brute Force Attacks
Brute force attacks try every possible numeric and/or alphanumeric combination to access a system. While the probability of getting a 6 digit OTP correct is 1/106 — literally one in a million — hackers use automated scripts to speed the process. They also can try the OTP for all users, so the likelihood of it working for one user increases. More secure methods of OTP authentication include controls that limit the number of login attempts making brute force attacks less likely. Still, determined hackers find ways to bypass rate limits and thus OTP security.
Phishing
Social engineering is a common method used to extract personal details from a victim for further use in other attacks. However, criminals have also started to leverage it as a tactic to steal OTP authentication codes and hack accounts. A recent phishing scam that targeted customers from eight U.K. banks and involved more than 7,000 phishing domains was able to bypass OTP authentication processes using techniques similar to the example below.
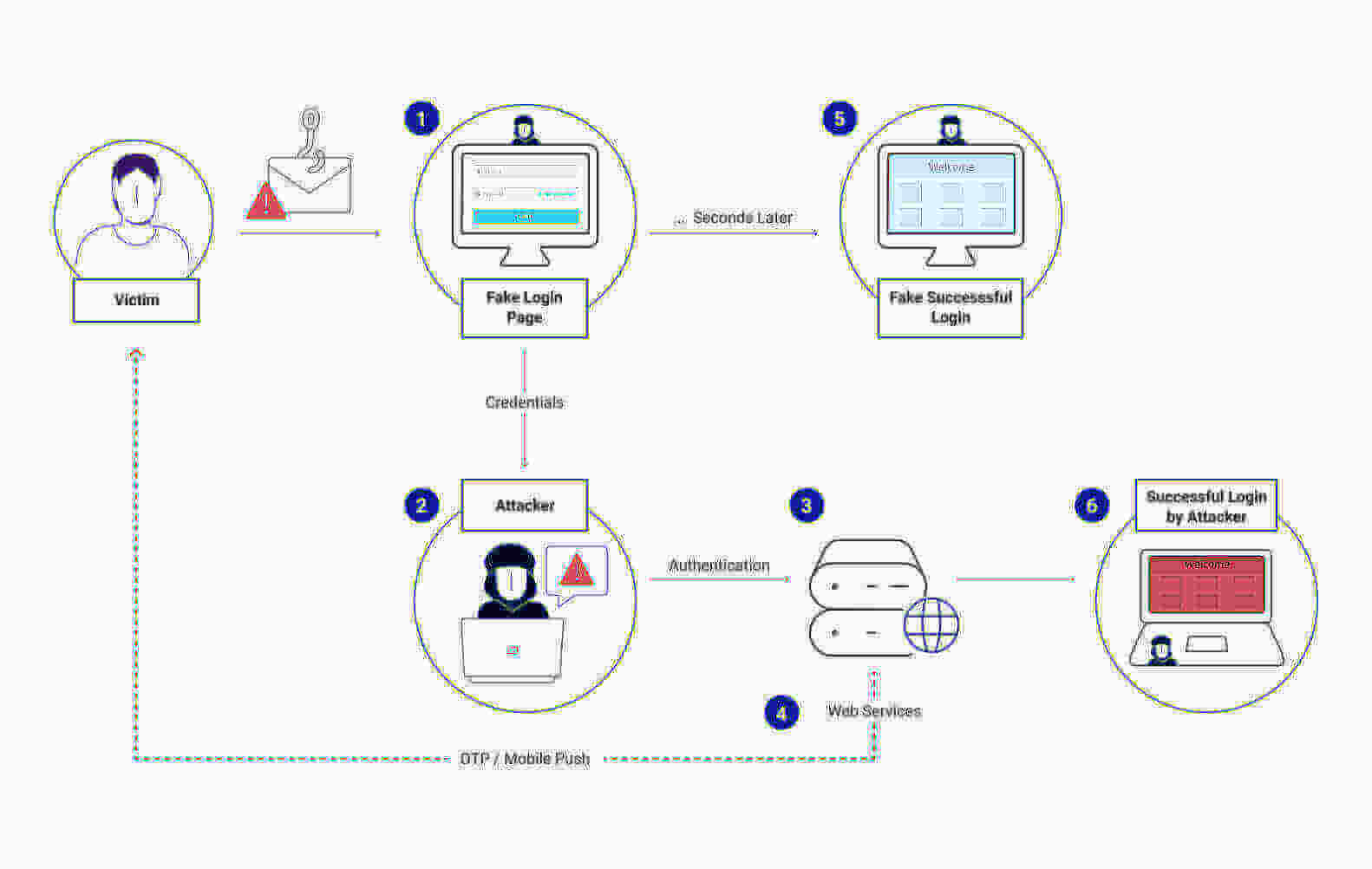
Example of How OTP Security Tokens Are Phished
- A convincing phishing email or SMS — claiming a suspicious payment for example — includes a link to a fake app or website.
- It looks like the real website so the user starts to log into their account, entering their name and password.
- The attacker captures this and starts a concurrent login process on the real app or website. The MFA flow sends the OTP to the victim via email or SMS.
- The user types the OTP security code into the fake app or site, the hacker grabs it and enters it into the real site, giving them account access.
- Meanwhile, the victim is directed to a fake successful login page or receives an error message.
Bonus: User Fatigue and Friction
Besides these common and varied attacks, OTP authentication methods also create significant user friction. The extra verification step disrupts the login flow and can lead to customers disengaging from your services completely. Server delays, missed messages and expired tokens all add to the frustration. Employees using OTP authentication waste valuable time simply accessing the resources they need to do their work. This friction also results in some people disabling OTP MFA if they can, since usability hurdles inspire workarounds.
What About Hardware OTP Security Tokens?
So far the discussion on what is OTP authentication and why it's failing has focused on software-based OTP security methods. For workforce authentication, you can also use hard tokens, usually in the form of key fobs or smart cards. These are certainly more secure than software OTPs but come with their own drawbacks. Costs can be significant, they are generally more difficult to deploy and users need to carry around a separate device — an even worse user experience than soft tokens. They also can still be bypassed through reverse-proxy techniques.
OTP Authentication vs. Passwordless MFA
Let’s be clear — any MFA is better than relying on passwords alone for account security. However, the widespread and documented successful attacks on OTP authentication protocols make it an increasing security risk for businesses.
Sometimes people refer to OTP verification methods as passwordless authentication but they are not While OTPs are dynamic and constantly changing, making them preferable to static credentials, they are still a password.
The best solution for achieving secure MFA is to remove all passwords — and their inherent vulnerabilities — from the equation. This can be achieved by utilizing HYPR's passwordless MFA, which leverages public key cryptography and a device’s hardware-backed secure execution environments. This is HYPR’s approach.
HYPR turns any ordinary smartphone into a PKI-backed security key for frictionless, secure authentication for customers or your workforce. HYPR incorporates strong user-possession and user-inherent verification into a single action without creating credentials that can be phished or otherwise compromised.
Schedule a demo to learn more about how HYPR is removing OTP authentication from MFA processes.
James Blantz
Head of Solutions Engineering, HYPR
James Blantz is the Head of Solutions Engineering at HYPR, where he leads enterprise deployments of passwordless authentication and identity assurance solutions. With over 17 years in cybersecurity, he previously held senior roles at Ping Identity, including Principal Solutions Architect, where he specialized in designing and implementing identity and access management systems.
Related Content

