Stay ahead of the curve with the latest news, ideas and resources on all things Identity Assurance and Passwordless.
What Is Phishing-Resistant MFA?
Highlights:
- Traditional multi-factor authentication has two major problems: friction and security. An alternative solution exists: Passwordless authentication. HYPR’s phishing-resistant passwordless MFA delivers the highest level of security while at the same time eliminating employee and user friction.
- There are a number of different methods for implementing phishing-resistant MFA to minimize the chance of attackers being able to bypass authentication. These include: Passkeys, security keys, and biometric authentication.
- Not every MFA solution will be suitable for your organization. You’ll need to evaluate it according to its flexibility, cost, scalability, and security strength.


Phishing, despite its somewhat innocuous name, remains one of the foremost security threats facing businesses today. Improved awareness by the public and controls such as multi-factor authentication (MFA) have failed to stem the tide.
The FBI Internet Crime Report puts phishing and its variants (spear phishing, smishing, vishing) as the top cybercrime for the last five years, and the advent of generative AI has only added fuel to the fire. Using ChatGPT and other tools, hackers can quickly create personalized messages, in local languages, to launch widespread, highly effective phishing campaigns.
In the last six months alone, malicious emails have increased by 341%, prompting industry experts to urge organizations of all sizes to implement phishing-resistant MFA.
So, what is phishing-resistant MFA and how does it differ from traditional MFA? In this article, find phishing-resistant definitions and use cases, and learn why it’s the safest option for organizations.
What is Phishing?
Phishing is a method of attack used by malicious actors that involves deceiving users into installing malware or revealing sensitive information such as passwords, payment card and social security numbers. With this information they can take over accounts, sell the information on the dark web, steal identities and even access internal systems and networks of an organization.
Common phishing attacks include:
- Email phishing: Attackers send emails, typically with malicious links or attachments that steal sensitive data from users.
- Whale and spear phishing: Similar to email phishing, whale and spear phishing are more targeted and aimed at specific, typically high-profile people in the organization (e.g. CEO or other executive).
- Smishing and Vishing (voice phishing): Smishing uses SMS messages while vishing uses either a mobile or landline, combining it with social engineering attacks.
- Domain phishing/impersonation: Attackers typically pretend to be well-established brands to gain users’ trust and divulge sensitive information.
- Malicious attachments: Attachments contain malware that infect systems and can trigger ransomware or other attacks that steal sensitive data.
What is Multi-Factor Authentication?
Multi-factor authentication requires at least two independent factors, knowledge, or something you know (e.g., password, PIN, security question), possession, or something you have (e.g., OTP code, device), and inherence, or something you are (e.g., fingerprint or other biometric marker).
It is different from two-factor authentication (2FA) in that 2FA requires an additional verification besides your username and password, but it doesn’t require it to be from a different authentication category like with MFA.
Phishing-Resistant MFA Overview
Phishing-resistant authentication does not use shared secrets at any point in the login process, eliminating the attacker's ability to intercept and replay access credentials and hardening the authentication process so that it cannot be compromised by even the most sophisticated phishing attacks. Passwordless MFA based on FIDO standards is considered the gold standard for phishing-resistant authentication by the OMB and other bodies.
Phishing-resistant MFA is based on public/private key cryptography and follows the guidelines published by the OMB in its M-22-09 Federal Zero Trust Strategy memorandum and the requirements for “verifier impersonation resistance” outlined by the National Institute of Standards and Technology (NIST) in SP 800-63-3.
The Problem With Traditional MFA
There are two different problems when it comes to traditional MFA. The first is that it causes friction, both for employees who use it to access accounts and consumers who want to make their purchases quickly.
The second problem is a security issue. Unfortunately, the most common second factor in traditional MFA is “something you have” in the form of an SMS or OTP. Like passwords, these verification methods are highly vulnerable to phishing as well as MitM (Man-in-the-Middle) attacks. In order for MFA to resist phishing, it cannot rely on the use of SMS, OTPs, or identification attempts through voice calls or interceptable push notifications.
Why Phishing-Resistant MFA is the Gold Standard
A better solution is FIDO or PKI-based passwordless authentication. These phishing-resistant MFA methods remove the vulnerabilities that undermine traditional MFA, including any use of a “something you know”’ factor as these are the target of the majority of phishing attacks.
Phishing-resistant MFA does not use any of these weaker authentication factors. It uses a strong possession factor in the form of a private cryptographic key (embedded at the hardware level in a user-owned device) and strong user inherence factors such as touch or facial recognition. Equally important, the backend authentication process does not require or store a shared secret.
Since 2022, CISA, the Cybersecurity and Infrastructure Security Agency, has strongly recommended that all organizations implement phishing-resistant MFA based on FIDO standards. This is considered the gold standard for phishing-resistant authentication by NIST (800-63B), the FFIEC, the OMB and other cybersecurity statutes.
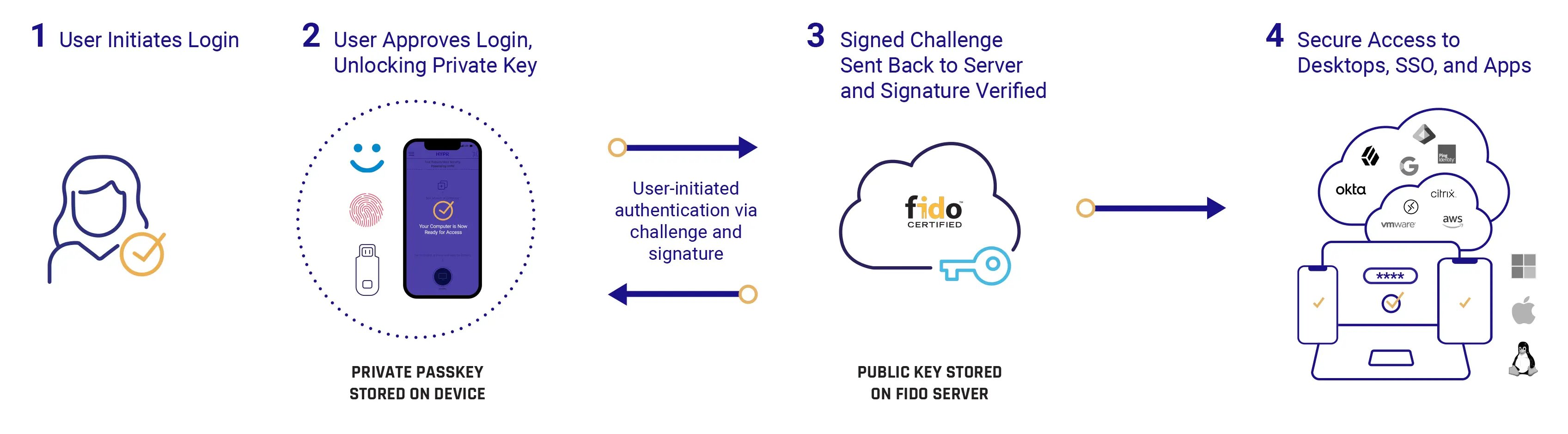 Phishing-resistant MFA flow
Phishing-resistant MFA flow
Breaking Down Phishing-Resistant Multi-Factor Authentication
Phishing-resistant multi-factor authentication defends against attackers who are looking to bypass authentication controls. This more advanced level of security involves various technologies and processes, which can be implemented in a number of ways.
Strong Authentication
A hallmark of phishing-resistant MFA is strong authentication that provides a robust defense against phishing and other targeted attacks. A somewhat broad concept, it involves using secure cryptographic protocols and two or more authenticating factors that include proof of device possession as well as user biometrics.
Passkeys
Passkeys replace passwords and secrets with cryptographic key pairs and on-device biometrics for faster, easier, and more secure sign-ins to websites and apps. Unlike passwords, passkeys are always strong and phishing-resistant. Passkeys can be either synced or device-bound. Synced passkeys are the standard passkeys offered by Apple, Microsoft, Google and others.
The private key is securely stored in a vault, such as the OS keychain or a password manager, and can be synced between devices. Device-bound passkeys, by contrast, are stored on a specific hardware device and cannot be shared with other devices.
Security Keys
Security keys are physical devices that store cryptographic keys, but they can be either hardware or software-based. Software-based keys might be stored and integrated into mobile devices, for example, whereas hardware keys are physical devices that store cryptographic keys. However, this method has limitations as it can easily be lost or stolen and challenging to recover.
Biometric Authentication
Biometric authentication focuses on biological methods of identification such as fingerprints or face recognition to verify identity for the inherence (e.g. “something you are”) authentication factor. It is often integrated into devices such as mobile phones or computers.
Adaptive Authentication
While not technically an element of phishing-resistant MFA, adaptive authentication enforces verification of identity based on the user’s context and risk. For example, it would have a different process based on the user’s location (e.g. home or work) and device (e.g. phone or work computer).
The Cost of Phishing Attacks
Phishing plays a role in various types of attacks. According to the 2023 Verizon Data Breach Investigations Report, phishing accounted for 44% of social engineering breaches, with the median amount stolen from Business Email Compromise alone averaging $50,000. It’s also a key initial attack vector in credential stealing, allowing hackers to initiate fraudulent transactions, deliver malware including infostealers and ransomware and gain an authenticated foothold from which they can move laterally within the system.
The Cost of a Data Breach 2024 report by IBM estimates that the average cost of a data breach is $4.88 million, an increase of 10% from the year before. Unfortunately, the go-to mitigation to prevent phishing, namely adding traditional MFA, has proven inadequate. Sometimes they are even used as part of the attack itself.
Most multi-factor authentication solutions feature a password as one of the verification factors. The additional authentication factor generally is a one-time password (OTP) sent by voice, SMS, or email, or a push notification via an authenticator app that the user must accept.
Today, automated phishing kits that can circumvent these methods are readily available to hackers. Cybersecurity experts claim that over 90% of all multi-factor authentication is phishable. Due to these MFA vulnerabilities and the threat posed by phishing, the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Government Office of Management and Budget (OMB), as mentioned above, have specifically called for phishing-resistant MFA.
Why Organizations Need to Prioritize Phish-Resistant Authentication
While the need for phishing-resistant MFA has been apparent for some time, and was a key driver for establishing the FIDO Alliance, the generative AI trend and ChatGPT in particular has kicked this into overdrive. Cybercriminals now have the ability to send massive numbers of highly targeted phishing attacks using dark web ChatGPT counterparts such as FraudGPT and WormGPT.
According to Slashnext’s State of Phishing 2024 Mid-Year Assessment, there has been a 4151% increase in malicious emails since the advent of ChatGPT in late 2022.
As phishing attacks have increased, so has the incidence of account takeover (ATO), leading to a number of potential consequences for targeted organizations, including supply chain fraud, data theft and the installation of ransomware and other malware. Attackers can also use the hijacked account of one user to escalate attacks within the organization by sending malicious emails from a trusted user.
Multi-factor authentication has proven ineffective against modern phishing campaigns, which are able to phish both the initial login credentials and the second factor. For example, a phishing message might direct the victim to a proxy website while the attacker acts as a man-in-the-middle to steal both the password and OTP code.
This is only one of many tactics cybercriminals use to compromise multi-factor authentication that uses OTPs or SMS. Others include running legitimate versions of websites on their own servers, using robocalls to convince users to hand over codes and SIM-swapping, so messages are sent to an attacker’s phone.
The skyrocketing number of phishing attacks in general, accompanied by sophisticated tactics that can circumvent common authentication checks, means that phishing-resistant MFA is no longer optional. Instead, it is the only choice to keep employees and organizations safe from the vast majority of phishing threats.
How to Choose a Phishing-Resistant MFA Solution
When considering a phishing-resistant MFA solution, you’ll want to ask about its ability to completely remove shared secrets (passwords, OTPs), its support for multiple devices (e.g. desktop and mobile), and its ability to reduce friction for the user experience.
For example, does it secure authentication for remote workers and work offline? Is it intuitive and easy for new users to learn? You’ll also want to verify how long it takes to deploy across your organization and if it integrates with major identity providers (IdPs). Finally, you’ll want to make sure its FIDO Certified and achieves compliance with Zero Trust architecture and regulatory obligations.
Considerations When Implementing Multi-Factor Authentication
Implementing multi-factor authentication within your organization involves a few different factors to evaluate:
- Security strength: Although MFA typically protects against brute force attacks, some types of authentication are subject to phishing attacks. To ensure the highest level of security, however, you’ll want to consider phishing-resistant MFA that is FIDO-compliant.
- Cost: You’ll need to evaluate the costs of the solution, which include not only setup and user training but ongoing maintenance costs. Keep in mind that while some solutions might cost more, they may also deliver better security and be easier for your team to implement. Some solutions may also impact productivity at the time of deployment, so that might be a consideration.
- Flexibility: Users want a number of different options available for MFA. Check that your solutions offer different methods of authentication, such as verification via a mobile application or hardware keys to adjust to the needs of different users and environments.
- Scalability: Can the solution adapt to the changing needs of your organization? Can it handle a workforce that is remote? Does it offer MFA for networks, servers, and cloud infrastructure?

Learn how to evaluate passwordless security solutions
HYPR's Phishing-Resistant MFA Solution
It’s clear that phishing-resistant MFA is critical, but what does it look like in practice? HYPR’s Passwordless MFA solution is based on the FIDO standards and provides phishing-resistant authentication from desktop through to cloud applications, no matter where your workforce is located.
HYPR leverages public key cryptography to allow for secure authentication that fully eliminates the use of shared secrets between parties. Just as importantly, the HYPR platform is easy to deploy and makes logins fast and easy for the user. Complicated sign-in processes are one of the biggest reasons that people take shortcuts or use unsafe practices that criminals exploit.
To learn more about passwordless security and phishing-resistant MFA, read our Passwordless 101 guide.
FAQs
What is the difference between passwordless and phishing resistant MFA?
Not all passwordless MFA is phishing-resistant or indeed really passwordless. OTP codes, after all, are a form of password. A solution that uses any kind of shared secret can still be compromised by phishing, man-in-the-middle and other attacks that target credentials. Phishing-resistant MFA, on the other hand, ensures that even if users are targeted with phishing attacks, there are no credentials available to steal and their authentication remains secure.
What are the benefits of phishing resistant MFA?
Phishing-resistant MFA delivers a number of benefits to the user. First, it delivers a friendly user experience that eliminates the friction involved in the traditional MFA process. Second, it provides a higher level of security than two-factor authentication or traditional multi-factor authentication.
Can phishing bypass 2FA?
Yes, phishing can bypass 2FA using a number of different methods such as man-in-the-middle attacks, password resets and social engineering attacks. This is because most 2FA verification methods involve one-time passwords (OTP) via email or SMS, which can be easily intercepted.
Why are passkeys phishing resistant?
Passkeys are phishing resistant as they are based on FIDO standards which were designed to resist phishing as well as some other forms of attack. They consist of cryptographic key pairs, which are registered to a specific authenticating service, ensuring that the passkey only works with the exact domain name of the service. There are no passwords or shared credentials to phish and a spoofed site cannot use them.
Editor's Note: This blog was originally published May 2022 and has been completely revamped and updated for accuracy and comprehensiveness.
Baljeet Sandhu
CTO
Baljeet Sandhu is the Chief Technology Officer at HYPR, where he leads the engineering behind its secure, passwordless authentication solutions. With over 20 years of experience in cybersecurity and software engineering, he has held senior roles at Barclays, Bank of America, and RBC. His expertise spans cryptography, cloud architecture, and API development, all essential to HYPR’s mission of building trusted identity systems.
Related Content

