Stay ahead of the curve with the latest news, ideas and resources on all things Identity Assurance and Passwordless.
How Secure is Critical Infrastructure?



Watch the presentation from CISA’s ICSJWG Spring Meeting: Recently, HYPR partnered with the CISA Industrial Control Systems Joint Working Group (ICSJWG) to examine the latest CISA guidance around identity and multi-factor authentication. While that spring meeting session is over, we re-recorded it for the general public.You can watch it here.
The usual cybersecurity focus on malware and ransomware has been quickly eclipsed by recent global events and the looming risks from foreign governments and rogue factions using digital weapons to access, manipulate and disable critical infrastructure. But critical infrastructure attacks are not new. Stuxnet, which reportedly impacted nuclear centrifuges, occurred all the way back in 2011. The difference now, however, is the frequency, severity and world environment today.
Recent Critical Infrastructure Cybersecurity Alerts Issued
This week, on April 20, 2022, the cybersecurity authorities of the United States, Australia, Canada, New Zealand, and the United Kingdom released a joint Cybersecurity Advisory (CSA) to warn Critical Infrastructure organizations that Russia’s invasion of Ukraine could spawn increased malicious cyber activity and critical infrastructure attacks by Russian state-sponsored cyber terrorists and cybercrime groups. In tandem, the Cybersecurity & Infrastructure Agency (CISA) issued Alert AA22-110A to address this topic, with technical details about threat actors, tactics used and recommended mitigations.
This follows on the heels of CISA’s Alert A22-083A, issued on March 24, on Tactics, Techniques, and Procedures of Indicted State-Sponsored Russian Cyber Actors Targeting the Energy Sector which occurred between 2011-2018. (The indictments were unsealed on March 24th, prompting guidance from CISA once declassification occurred.) A critical adjunct to both of these warnings is the Shields Up program, launched in February, which put all organizations on a heightened state of alert.
The relatively short amount of time to issue these two alerts, the establishment of the Shields Up program, and the joint warning issued by five countries, should be indicative of the clear and present danger to critical infrastructure organizations and a rallying cry to proactively address the threat with improved critical infrastructure cybersecurity.
What Can We Learn From Recent Attacks?
These are a sample of critical infrastructure attacks over the past several years. Although not all targeted critical infrastructure specifically, they each impacted it in some way:
- 2014 – Dragonfly - Campaign
- 2015 – Ukraine Power Grid
- 2016 – Ukraine Power Grid #2
- 2016 - San Francisco Muni System
- 2017 – Crashoverride Malware
- 2017 - Saudi Petrochemical
- 2019 – Kudankulam Attack
- 2020 - Israeli Water Systems
- 2021 - Oldsmar Water Treatment
A notable critical infrastructure attack that I omitted from the list above was the well-publicized Colonial Pipeline ransomware attack, which shut down the pipeline that runs from Texas to New Jersey. While the disruption was relatively short, fuel prices skyrocketed and minor consumer panic ensued — and this was a couple of days rather than weeks or months.
How did actors gain access to the pipeline? Post mortem investigations and testimonies on the Hill found that the origin of the infamous critical infrastructure attack was based on the lack of proper authentication safeguards. In fact, in the Colonial Pipeline incident, multi-factor authentication (MFA) was never implemented on the compromised account. This was the crack in the armor that attackers exploited. Further investigations revealed that while defense contractors should have also implemented MFA five years ago, many have not fully implemented it. In fact, MFA projects frequently exist on a planning chart only.
Where Do We Go From Here?
In 2021 CISA adopted a Zero Trust model represented below, which lays out a framework for protection of environments against critical infrastructure cybersecurity threats that can literally obliterate them.
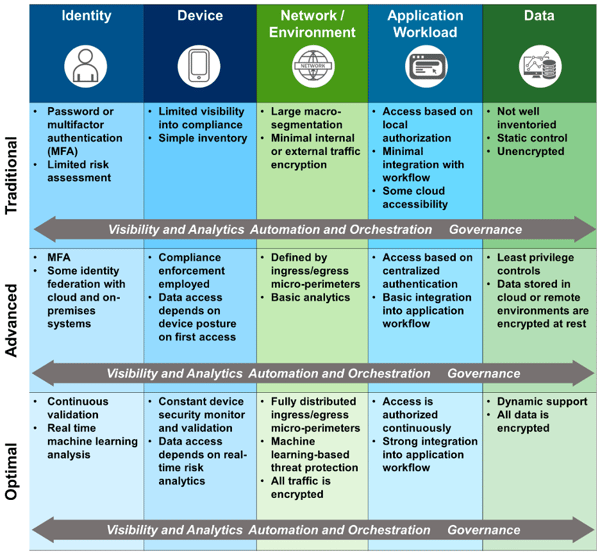
(Source: CISA)
It is a lot to digest and it is easy to get overwhelmed. Nevertheless, the entry point for some of the most well known SCADA and critical infrastructure attacks starts with authentication. MFA is essential to ensure that rogue elements cannot enter your digital realm. It is called out front and center in the Zero Trust model. When it comes to critical infrastructure cybersecurity, here are three areas under the authentication category to implement as soon as possible along with my recommendations on how to achieve this.
Multi-Factor Authentication
CISA Guidance: Enforce multi-factor authentication (MFA) by requiring users to provide two or more pieces of information (such as username and password plus a token, e.g., a physical smart card or token generator) to authenticate to a system.
A Best Practice Approach: MFA can greatly reduce unauthorized access but to truly secure against phishing, smishing, man-in-the middle, account takeover and push fatigue, consider next-generation passwordless multi-factor authentication (PMFA). PMFA completely eliminates shared secrets by storing a private key on each user’s device. A public key is stored in the cloud. Authentication is initiated by the user and is executed via challenge and signature, with passwordless MFA into desktops, VPN and SSO. This type of frictionless phishing-resistant MFA conforms to the FIDO standard which is recognized by the OMB and CISA as the gold-standard for Zero Trust Authentication.
Privileged Account Management
CISA Guidance: Manage the creation of, modification of, use of — and permissions associated with — privileged accounts, including SYSTEM and root.
A Best Practice Approach: Your PFMA solution should deliver a seamless authentication experience from the desktop to the cloud. Both a desktop as well as an application element is crucial in critical infrastructure environments since SCADA devices and HMIs are often a shared workstation which may be used by many. Once a user has successfully authenticated, additional logins are unnecessary thus creating a seamless user experience while remaining secure throughout all operations. Look for a solution which can provide this on all supported operating systems to eliminate potential holes in Zero Trust implementation.
Password Policies
CISA Guidance: Set and enforce secure password policies for accounts.
A Best Practice Approach: Phishing and credential stuffing attacks exploit passwords and its reuse. A 2021 survey revealed that 65% of people reuse passwords across accounts, and nearly half hadn’t changed their passwords in over a year, even after a known breach. Instead of typing in passwords PMFA graduates organizations to advanced password policies and phishing resistant MFA (recommended by OMB) for authentication security with lightning-speed passwordless authentication.
In Conclusion
We are at an inflection point where environments face seriously increased risk of critical infrastructure attacks. By proactively aligning with guidance from CISA and other security agencies, we can apply critical infrastructure cybersecurity best practices to secure our environments where recent events have proven they are most vulnerable. Adopting PMFA not only provides the security required to ensure the resiliency of our critical infrastructures so they do not become the next battleground for entities looking to harm your organization and society that depends on you.
To learn how HYPR True Passwordless™ MFA can solidify your critical infrastructure cybersecurity, contact our team.
Joshua Gonzales
Senior Product Marketing Manager
Joshua Gonzales is a Senior Product Marketing Manager at HYPR, where he helps position the company’s authentication solutions in the identity security space. He previously led go-to-market strategies at cybersecurity companies such as Beyond Identity, and also worked as a social media consultant for major brands including HarperCollins and Express. Joshua’s background in cybersecurity and digital storytelling helps convey the importance of eliminating passwords and building trust in the identity lifecycle.
Related Content
