Stay ahead of the curve with the latest news, ideas and resources on all things Identity Assurance and Passwordless.
How to Use Context-Based Authentication to Improve Security



One of the biggest security weak points for organizations involves their authentication processes. According to Google Cloud’s 2023 Threat Horizons Report, 86% of breaches involve stolen credentials. Our own research found that 60% of organizations reported authentication-related breaches in the past year. Context-based authentication offers an important tool in the battle against credential stuffing, man-in-the-middle attacks, MFA prompt bombing, and other attacks on authentication systems.
Also referred to as adaptive authentication or risk-based authentication, context-based authentication layers on dynamic security controls that use contextual signals and other indicators of risk to make access decisions. When used in conjunction with secure passwordless authentication, it helps better protect your resources while providing better employee and customer login experiences.
What Is Context-Based Authentication?
Context-based authentication goes beyond traditional methods by controlling access and user authentication flows based on dynamic risk calculations. It analyzes information such as user behavior, device signals, and risk signals from other security tools to dictate access policies. This is a departure from traditional authentication, which relies solely on presenting the correct credentials. Based on this risk information it may, for example, prompt users for an additional authentication factor, require them to re-affirm their identity through a proofing process, or block access altogether. Incorporating context and eliminating insecure passwords from the authentication process significantly reduces the risk of unauthorized access, thereby lowering the chances of a potential data breach.
In its simplest terms, context-based authentication involves two parts:
- Establishing a baseline: In order to determine what behavior and scenarios are suspicious, the systems must first establish a baseline for each user that defines what is normal.
- Responding to anomalies: Once a baseline is set, the context-based authentication system evaluates each login attempt against this norm. It actively scans for potential anomalies, such as login attempts originating from unusual geographic locations or suspicious VPNs, during periods of user inactivity, if the device is rooted or jailbroken, and other factors that indicate a higher risk. It also takes into account the type of access requested — for example a high-risk transaction. If elevated risk levels are detected, the system triggers additional authentication factors or verification steps.
Key Components of Context-Based Authentication
Any context-based authentication system contains these basic components, although they will vary in both how they are constructed and how they get used. The best context-based authentication processes assess multiple layers and signals in order to effectively optimize for both security and user experience.
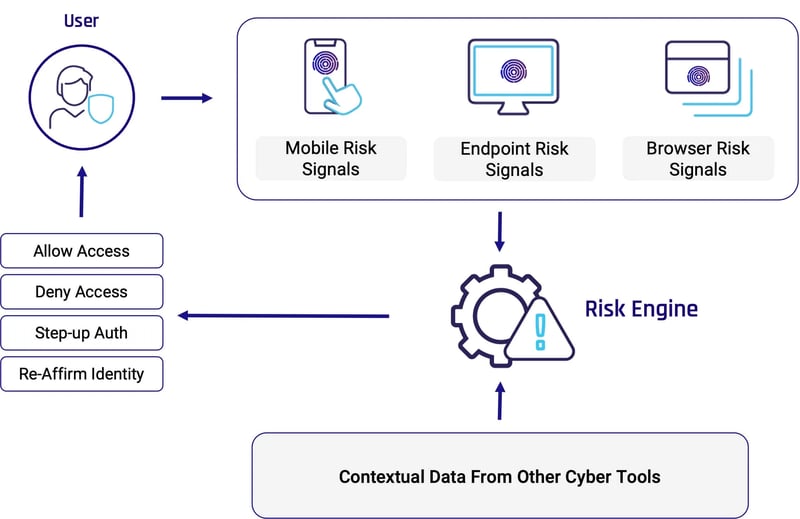
Risk Engine
The heart of context-based authentication is the risk engine. The risk engine continuously collects and analyzes data to determine the risk level associated with each user access request. Modern authentication risk engines use machine learning algorithms and artificial intelligence to detect malicious behaviors and threats in real time. The broader and more varied the information sources and risk signals, the more accurate and effective the risk engine.
Context Sources
As mentioned, the effectiveness of the risk engine fully depends on its data sources. Sources include things such as device health posture, mobile, web and browser contextual signals, real-time events, user behavior and access patterns. Ideally, your sources also include risk data from EDR systems and other cybersecurity tools deployed in your organization.
Action Orchestration
Real-time risk information holds little value if it cannot also be actioned upon in real time. Context-based authentication systems use the risk insight to enforce access policies. This can range from simply denying access, to requiring additional authentication steps, to requiring the person to prove that they are the person they claim to be using identity verification technologies.
Benefits of Context-Based Authentication
Context-based authentication provides multiple advantages for organizations.:
- Prevents attacks: Context-based authentication operates as a continuous gatekeeper, actively scanning for anomalies and high-risk activities. This proactive approach prevents unauthorized access attempts and significantly reduces the risk of successful attacks, protecting sensitive data and fortifying the organization's security posture against evolving threats.
- Improves User Experience (UX): By leveraging contextual cues to streamline access, it ensures that legitimate users can navigate seamlessly through the authentication process. This not only enhances overall user satisfaction but also minimizes friction, making security measures more user-friendly without compromising on protection.
- Ensures Regulatory Compliance: Context-based authentication allows organizations to continuously assess identity threats and mitigate risks as required by NIST, ISO, HIPAA, GDPR and other regulations. It also can ensure only authorized users access sensitive information in accordance with requirements under PCI-DSS, FISMA, FRCP and HITECH.
- Enables Zero Trust Architecture: Context-based authentication aligns with Zero Trust “never trust, always verify” principles. It assumes that no user or system is inherently trustworthy, requiring continuous and ongoing verification. When used in conjunction with phishing-resistant AAL3-compliant authentication methods, it provides a strong foundation for building a Zero Trust architecture.
Implement Context-Based Authentication With HYPR Adapt
Context-based authentication employs risk-based analysis to determine and adjust authentication security controls in real time. The level of security it delivers depends on multiple factors including the sophistication of the risk engine, the breadth and depth of contextual information it uses, and the range of security controls it can affect.
HYPR Adapt leverages a cutting-edge identity risk engine for real-time threat assessment, dynamically adapting security policies to deliver a personalized yet secure authentication experience. HYPR Adapt operates in tandem with HYPR's industry-leading, FIDO-based passwordless MFA solution, delivering a powerful risk-based authentication solution that tailors workflows to each user's context, effectively mitigating risks. For details, download the product brief or contact an authentication security expert for a free demo.
FAQs
Q: What is context-based authentication?
A: Context-based authentication utilizes risk-based analysis to determine the appropriate authentication level, adjusting identity security measures based on real-time user actions and threat assessments.
Q: How does context-based authentication enhance security?
A: Context-based authentication enhances security by dynamically adapting to changing risk levels, providing a personalized authentication experience tailored to each user's unique context, thereby effectively mitigating potential risks.
Q: What are some real-world scenarios for using context-based authentication?
A: Adapting authentication flows to contextual information becomes especially crucial in situations such as remote worker access, to evaluate and act on indicators of elevated risk. Another important scenario is to add extra levels of security on financial transactions, such as transferring or withdrawing funds.
Q: What is HYPR Adapt, and how does it facilitate context-based authentication?
A: HYPR Adapt dynamically assesses potential identity threats and enforces adaptive security controls so you can effectively manage identity-related risks, even in rapidly changing environments. Its powerful risk engine analyzes signals and telemetry from numerous sources, including user behavior analytics and contextual information from mobile, endpoint and browser signals. Results can be used to enforce step-up authentication, prompt re-verification or deny access altogether, as well as shared with SIEM, SOAR and other enterprise systems.
Joshua Gonzales
Senior Product Marketing Manager
Joshua Gonzales is a Senior Product Marketing Manager at HYPR, where he helps position the company’s authentication solutions in the identity security space. He previously led go-to-market strategies at cybersecurity companies such as Beyond Identity, and also worked as a social media consultant for major brands including HarperCollins and Express. Joshua’s background in cybersecurity and digital storytelling helps convey the importance of eliminating passwords and building trust in the identity lifecycle.
Related Content

