Stay ahead of the curve with the latest news, ideas and resources on all things Identity Assurance and Passwordless.
Using "Approval-as-Code" in Access Management



In today's modern work environment, effective management of user identities and access is crucial for securing enterprise applications, systems, and data. As organizations increasingly deploy cloud-based services and resources, managing access has become complex and necessary. As a helpdesk engineer, it’s my responsibility to manage and track access requests from end users. To streamline this process and ensure secure access, I recently deployed an approval-as-code tool, which automates the approval process for access requests and integrates with our existing tools. This will enhance our ability to manage access and mitigate the risks associated with unauthorized access to critical systems and data.
Access Management Challenges
Traditionally, I provide users with predefined default access based on their roles and responsibilities. Some admin users are provided with full access to core resources on an ongoing basis. Unfortunately, these accounts are potential targets for security breaches. Experian, Uber and Okta, and many others, were all breached due to hackers, such as the Lapsus$ group, exploiting admin access.
In some emergency situations, users are provided with elevated access to be able to resolve a critical issue or incident. These requests are largely handled in either tickets or Slack threads. In other words done “by hand”.
Some of the challenges I face:
- Inefficiency: Manually managing access can be an inefficient process and mistakes can be made if access is not removed.
- Compliance challenges: It can be difficult to demonstrate that access controls are being enforced when some users have perpetual admin access.
- Scaling: As the organization grows and the number of users and resources increases, it becomes more difficult to manage access for a large number of users across many systems. Creating access policies can get complex.
What Is Approval-As-Code?
At HYPR, Infrastructure-as-Code (IaC) is an already adopted practice to automate and standardize the process of deploying and managing our IT resources. We recently came across a tool that advertises “approval-as-code,” which extends the same principles as Infrastructure as code. With approval-as-code, we can automate and codify approval workflows for elevated access.
The tool in question is called SYM by a company called SYMOps. Sym allows you to build approval workflows that can be initiated and approved within Slack to dedicated resources defined within the tool. This provides just-in-time access in a manner which is audited and tracked. The current approval flow we have in place:
- End users request access within Slack and are asked
- Which resource they need access to
- Justification (ticket, incident or reason)
- Duration of access
- Request is routed to a dedicated Slack channel
- Designated approvers can either approve or deny the request
- If approved, the user is provided access to the resource for the duration selected
- Once the time for the duration expires, access is removed and the user is notified within Slack.
Being that SYM is approval-as-code, we use our current code review process and I can collaborate with my team when building the workflows. The tool itself is managed with Terraform code so you can deploy resources and update the workflows. The approval logic is all defined in Python code so I am able to create custom policies that meet our needs but also help us scale.
Deployment
Now I am not a strong or even an average coder, but the examples and support provided by the SYM team has been invaluable in helping my team and I get this tool off the ground running. No question was too basic or complex for their team as they helped me craft this tool which is now critical for our daily operations.
SYMops offers multiple out-of-the-box integrations with their Python libraries. With the custom logic, we are taking advantage of the PagerDuty integration. This integration on request checks if the user is on-call in PagerDuty, to assist with “break-glass” access after hours in response to an incident or a page. Here is an example of the code that defines this logic which is also in the examples SYMOps provides:
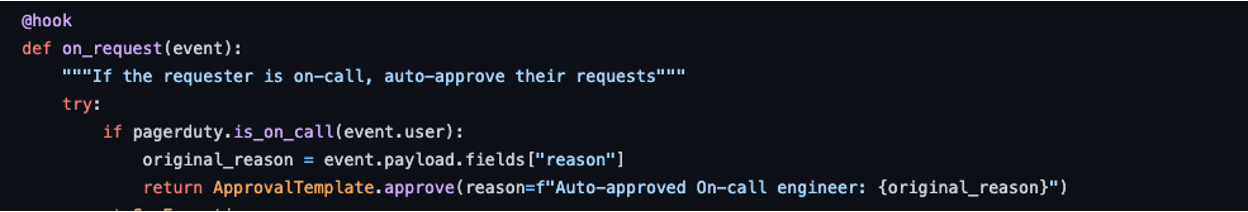
https://github.com/symopsio/examples/tree/main/basic/pagerduty_on_call
Greater Security, Greater Convenience
By implementing a tool like SYM on top of our HYPR Passwordless stack, we can improve the speed, tracking and security of our applications, systems and data. Being that the tool is built within Slack allows our organization to easily adopt this process and not impede any critical work or velocity of our teams. Having the elevated access being gated by the approval workflows helps us ensure that there are sufficient guardrails for access controls in place and they are enforced.
Anton Gurov
CISO
Anton Gurov currently serves as HYPR's CISO, focusing on Security, Compliance and Operations. Anton’s industry background is in mobile payments, ad tech and cloud management, with direct experience in PCI-DSS/SOC2/ISO/GDPR/CSTAR compliance in private/hybrid and cloud-native organizations. His career contributions led to 3 successful startup exits totaling $1.1B+. Anton had exposure to NIST standards and controls while pursuing FedRAMP at VMware.
Related Content
