Stay ahead of the curve with the latest news, ideas and resources on all things Identity Assurance and Passwordless.
5 Key Takeaways From the NSA and CISA IAM Guidance



On October 4, 2023, the Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA) jointly released new guidance titled Identity and Access Management: Developer and Vendor Challenges, which addresses technology gaps that limit adoption of more secure identity and access management (IAM) practices. This guidance is a follow on to their comprehensive guidance report on IAM published earlier this year. Together, these documents describe key principles and best practices to fortify organizations against the rising tide of cyberthreats.
The NSA / CISA IAM guidelines covers deterrence, prevention, detection, damage limitation, and response. Here, we'll explore key takeaways from the reports as well as how HYPR, with its Identity Assurance approach, helps you overcome challenges to successfully align with the recommended NSA / CISA IAM security strategies.
IAM Threat Landscape
One of the most significant threats trends in the past few years is the specific targeting of IAM systems and processes. According to one recent study, 90% of organizations experienced an identity-related incident, ranging from phishing and credential theft to man-in-the-middle attacks.
The NSA / CISA IAM guidance points out that attacks on SSO technology, in particular, have become more prevalent. By compromising SSO systems, cybercriminals can gain access to numerous protected applications and resources throughout an organization. The agencies state that defense against such a broad range of attacks requires a comprehensive solution “with operational awareness of the environment to detect anomalies and attribute anomalous activity to adversary exploits.”
Key Takeaways From the NSA / CISA IAM Guidelines
1. Enterprises Must Look at the Entire Identity Lifecycle
The guidance stresses the importance of managing the entire identity and access lifecycle, emphasizing "Join, Move, and Leave" (JML) events. The report notably calls out the inadequacy of MFA enrollment processes that make it difficult to be certain that a user’s credentials are tied to an established, verified employee identity. Such processes often rely on user self-enrollment that utilize inconsistent and insecure methods such as a “one time enrollment code” flow.
The directives recommend that organizations develop secure enrollment processes which can support the complex provisioning needs of large organizations, with tools that operate across systems and JML lifecycle events. These processes should also address unexpected events, such as detecting and responding to abnormal user behavior or other potential risks, and lost or stolen authenticators or devices.
In addition, the NSA / CISA IAM report strongly recommends organizations maintain an audit trail or a “chain of evidence” by requiring the manager or designated individual to “attest” to the fact that all required checks passed to the manager’s satisfaction.
2. Hardening the Enterprise Environment
The guidance emphasizes the need to harden the enterprise environment, including “making sure the foundations and implementations of IAM are sufficiently secured, assured, and trusted."
Environmental hardening makes it tougher to exploit IAM components and software. While some of the recommendations center around physical hardening and general cyber hygiene, like regular patching and vulnerability testing, a key component of enterprise hardening is the use of strong, phishing-resistant multi-factor authentication (MFA) for access to IAM systems. Moreover, cryptographic keys used for authentication and other IAM functions should be protected at appropriate assurance levels, preferably using hardware-based methods.
3. Authentication Best Practices: Strong, Phishing-Resistant MFA
Unsurprisingly, the NSA / CISA IAM recommendations unequivocally state the need for organizations to deploy MFA to mitigate common attacks. The agencies distinguish between weak and strong, phishing-resistant forms of MFA, noting that critical implementation details impact the security and usability of an MFA deployment. Some forms of MFA are susceptible to phishing, replay, MitM and other attacks. The guidance specifically warns against push notification-based authenticator apps that prompt the user to approve login attempts as these are susceptible to push notification attacks (MFA bombing). It advocates for local biometric matching on mobile devices and emphasizes FIDO-certified device requirements.
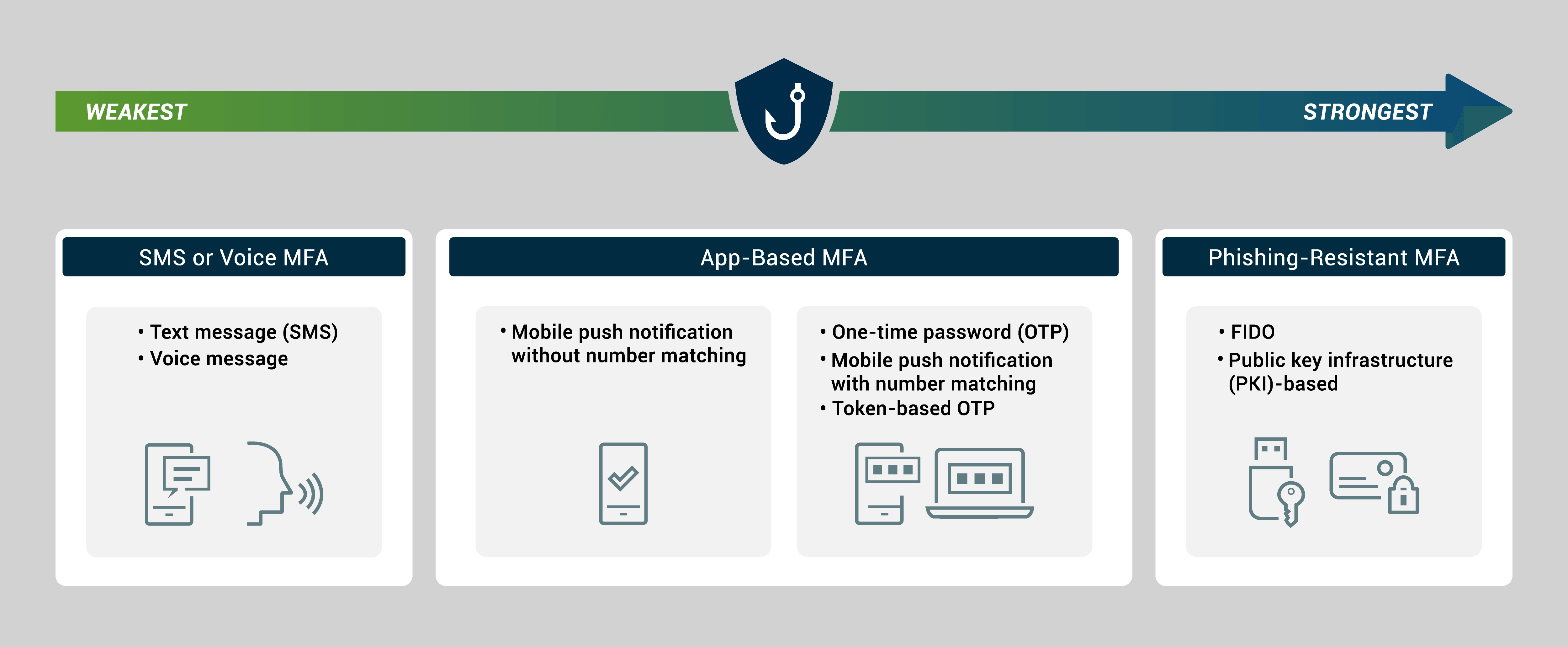
Weakest to Strongest Types of MFA
Source:The National Security Agency (NSA) and the Cybersecurity Infrastructure Security Agency (CISA)
4. Coverage Is Key
Before deploying MFA and monitoring solutions, understanding the full scope of use cases is crucial. The NSA / CISA IAM guidance warns against an ad-hoc approach that may lead to incomplete coverage and a complex environment. Multiple IAM systems and the use of different authenticators creates adoption challenges and confusion for users, as well as management and security monitoring difficulties.
This is currently a tremendous challenge for organizations. According to the 2023 IDSA report, the biggest obstacle to implementing more secure identity practices stems from complicated identity frameworks with multiple vendors and different architectures. Organizations should choose a comprehensive solution that can unify siloed systems and supports all of their business and operational use cases.
5. Respond to Elevated Risk
Because security and threat vectors are dynamic, the guidance advises organizations to implement automated risk analysis. Of course, quantifying risk is based on the policies that are in place. As such, the guidance highlights the requirements for policies that can trigger the need to re-authenticate or perform step-up authentication (i.e., requiring higher-assurance authentication than was used to initially establish a user’s session) when users access sensitive applications or perform high-risk activities. This provides the flexibility to require high assurance when needed without frustrating users engaged in routine, low-risk tasks with repeated MFA prompts. It also provides an integration point for Zero Trust Architecture (ZTA) policies such as requiring re-authentication or step-up based on risk signals from threat defense systems.
How Organizations Can Meet the NSA and CISA IAM Provisions
The release of CISA and NSA's new guidance on Identity and Access Management underscores the critical role identity security plays in fortifying cybersecurity defenses. As organizations navigate the complexities of an ever-changing threat landscape, adhering to recommended best practices is essential.
HYPR's Identity Assurance Platform, consisting of HYPR Authenticate, HYPR Adapt and HYPR Affirm, ensures IAM security aligns with the CISA/NSA guidance. Designed to create trust in the entire identity lifecycle, it combines modern passkey-based authentication with adaptive risk mitigation, automated identity verification and a simple, intuitive user experience.
- HYPR Authenticate provides the most secure FIDO-based, phishing-resistant MFA. It ensures that biometric templates are bound to a single device, mitigating privacy and security concerns and adhering to the best practices recommended by CISA and NSA. It provides complete coverage across all populations and use cases, from desktop to cloud.
- HYPR Adapt stands out by providing a flexible policy framework based on the Open Policy Agent (OPA) standard. This empowers organizations to create policies aligned with their risk criteria. HYPR's policies can dynamically trigger re-authentication or step-up authentication based on risk signals, in accordance with Zero Trust Architecture policies.
- HYPR Affirm integrates intelligent identity verification into an organization's identity and authentication practice, covering all JML events as well as high-risk and high-impact moments. This includes “new device” capabilities, where users can effortlessly but securely disable a device and move to a new one, verifying identity through a multi-faceted check that ensures the integrity of the device and the identity of the user. Moreover, it maintains an auditable attestation trail in alignment with NSA and CISA best practices.
To learn more about the NSA / CISA IAM guidance and how HYPR helps you comply, get in touch with one of our identity security experts.
Joshua Gonzales
Senior Product Marketing Manager
Joshua Gonzales is a Senior Product Marketing Manager at HYPR, where he helps position the company’s authentication solutions in the identity security space. He previously led go-to-market strategies at cybersecurity companies such as Beyond Identity, and also worked as a social media consultant for major brands including HarperCollins and Express. Joshua’s background in cybersecurity and digital storytelling helps convey the importance of eliminating passwords and building trust in the identity lifecycle.
Related Content
