Stay ahead of the curve with the latest news, ideas and resources on all things Identity Assurance and Passwordless.
Securing Your Linux Servers With HYPR



Securing your Linux servers is crucial as they often contain a company’s most valuable data and run the most critical services. One of the most effective ways to secure Linux servers is to add MFA and eliminate shared secrets that can be phished. It's also essential to have some type of step-up when invoking administrator privileges, like sudo or su.
Linux Server Authentication Security Challenges
Installing traditional MFA on a broad range of Linux/UNIX servers can be very challenging. Worse yet, many of the MFA providers currently on the market are using phishable second factors like SMS or OTP.
Any authentication factor that is stored outside of the device TPM, or ever in transit, can be phished, breached or intercepted. This includes one-time passwords (OTP) and text messages (SMS). On the other hand, credentials that never leave the device, such as cryptographic keys, or those that are unique to the individual, like locally stored biometrics, are not vulnerable to such attacks. It is important to understand the difference between these types of data and to take the necessary precautions to protect them. Using biometric authentication or hardware security keys can provide additional layers of protection for sensitive information.
Phishing-Resistant Passwordless MFA
HYPR is fully passwordless and phishing resistant; it eliminates the need for shared secrets of any kind. HYPR is also inherently multi factor, combining what you have — a FIDO Certified digital smart card running on your smartphone — with what you are. This takes the form of a biometric second factor, such as face recognition, fingerprint readers, etc.
HYPR for Linux
HYPR for Linux works as a standard pluggable authentication module (PAM) that can be used by services like SSH. Linux PAM provides a flexible way to perform authentication tasks. When a user logs in, the authentication process is managed by PAM and the modules it uses. Each module provides a specific authentication function, such as checking a password against /etc/shadow or using smart card authentication. The PAM configuration file specifies the modules to be used and their order, for a given service.
During authentication, PAM calls each module in the specified order until one succeeds or all modules have failed. This allows for easy addition or change of authentication methods without modifying the application itself. Overall, PAM enhances the security and flexibility of the Linux authentication process.
Installation of HYPR on Linux is a matter of obtaining the correct package; we have RPMs and DEBs available for most common Linux distributions. The following is an example of /etc/pam.d/sshd configuration with HYPR:
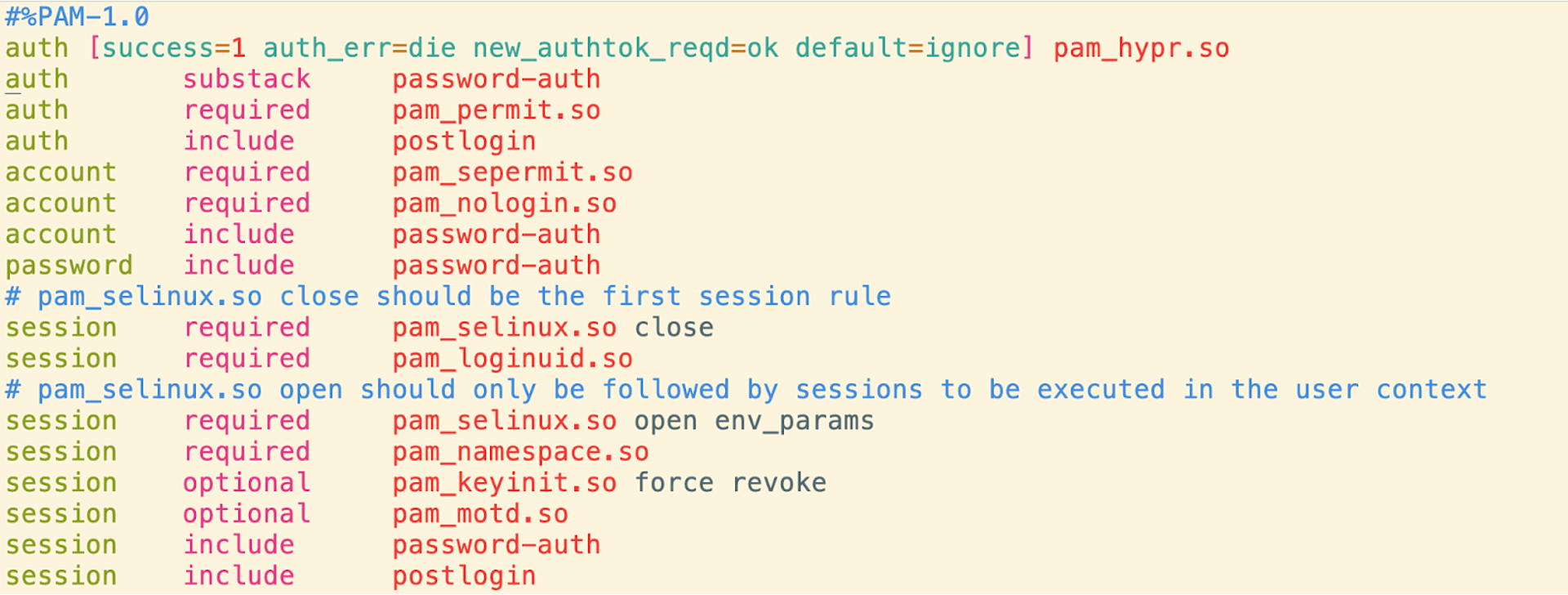
How does HYPR secure Linux servers? In this video, we demonstrate SSH login into a remote Linux server and step-up authentication when the sudo command is used.
Related Content
