Stay ahead of the curve with the latest news, ideas and resources on all things Identity Assurance and Passwordless.
Microsoft’s SFI: A Blueprint for Identity Security


A few weeks ago, Microsoft issued its first Secure Future Initiative Progress Report. Launched in November 2023, the Secure Future Initiative (SFI) is Microsoft’s acknowledgement that it needs to drastically improve its cloud security posture and make cybersecurity its top priority. The company has dedicated a substantial chunk of its engineering workforce to the effort ”to address the increasing scale, speed, and sophistication of cyberattacks.” In line with this mandate, a key area of focus is the protection of identities and secrets.
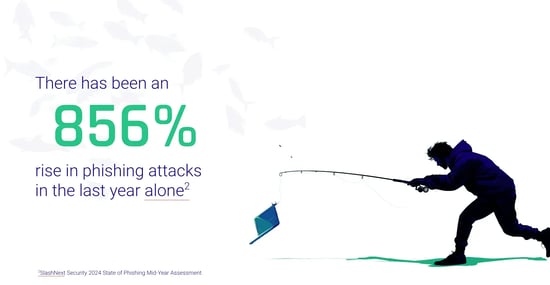
Identity security continues to be the weakest link in the cyber defenses of the vast majority of organizations. According to recent research, over three-quarters of companies have been hit by identity-related attacks and 69% were breached through authentication processes. One of the main incidents prompting the formation of the SFI was an attack campaign by Storm-0558, in which the threat group used a stolen key that creates multi-factor authentication codes to break into the Microsoft 365 accounts of more than 25 organizations, including government agencies.
It’s encouraging to see that identity security places prominently in the progress report, with several key areas noting improvement.
Phishing-Resistant Authentication as a Baseline
As an organization, Microsoft is making the move to phishing-resistant authentication, using passkeys or certificate-based authentication. They started with their production environment and are in the process of adoption and enforcement across all users in the productivity environment. This is exactly the right approach — tackle your most critical/at-risk systems first and roll out to the broader workforce in stages.
A phased method also fosters user acceptance. We’ve seen time and time again that passkey adoption gains a momentum of its own when users hear from their peers that it actually makes login faster and simpler.
New Critical Control: Video-Based Verification
Perhaps the most interesting aspect of their identity security overhaul is how they now handle credential recovery situations. Although the industry widely acknowledges that knowledge-based factors are insufficient for verifying employees' identities, many organizations have yet to take action. Microsoft, however, has shifted to using video calls for user verification, aligning with the NIST 800-63-4 identity proofing guidelines for IAL2. Currently in its second public draft, NIST 800-63-4 provides important updates from 800-63-3 to combat modern identity threats leveraging new technologies and best practices.
By forcing video verification for credential recovery, Microsoft now effectively shuts down one of the fastest growing attack vectors, help desk social engineering. The $100 million dollar attack on MGM Resorts occurred when hackers convinced help desk personnel to reset an employee’s credentials to grant them access.
Here’s an example of what such a video-based credential recovery process could look like.
Improving Secrets Management
While authentication is a critical part of identity security, secrets management is just as important. Secrets — like API keys, encryption keys, and access tokens — are often the target of sophisticated threat actors. Large organizations like Microsoft, which deliver many services, often struggle with secrets management. The problem is only growing as enterprises are building more applications, more quickly, aided by large language models (LLMs). The SFI emphasizes the need to make secrets management and security a top priority.
This includes using hardware-based protection to store secret keys and tokens, automated rotation of secrets, and increasing visibility into the context and usage of secrets. This kind of telemetry is essential to detect misuse and forgeries. According to the progress report, Microsoft has completed implementing hardware-based storage for signing keys for public and US government clouds, and has made significant headway on the remaining fronts.
The Role of Automation in Identity Security
Automation is becoming a crucial tool in the fight against identity-related attacks. In the SFI report, Microsoft outlined how they are leveraging automation to detect and respond to identity threats in real-time. From automatically identifying suspicious login behaviors to auto-locking compromised accounts, automation ensures that potential threats are addressed quickly — before they can cause significant damage.
Organizations can adopt similar strategies by integrating automated identity protection tools that monitor user activity and enforce security policies consistently across all users and systems. These tools can help reduce human error and ensure faster response times to identity threats.
Action Steps for Enterprises
Microsoft’s SFI serves as a reminder for all security and engineering teams to uphold rigorous security standards and adhere to the latest industry best practices. In particular, organizations should take heed and prioritize identity protection in their own security roadmaps.
For businesses looking to take a page from Microsoft's playbook, here are a few key actions to consider:
- Adopt Phishing-Resistant MFA: Transition away from traditional authentication methods, such as passwords and SMS-based MFA, to phishing-resistant options like passkeys (synced or device-bound) or certificate-based authentication.
- Implement Video-Based Verification: Follow Microsoft's lead and consider adopting video-based identity verification for critical credential recovery processes to combat social engineering threats.
- Leverage Automation: Use automated tools for identity verification, risk mitigation, and response to suspicious activity. Automation can act as a force multiplier for your security team, catching threats they may otherwise miss.
- Enhance Secrets Management: Ensure that secrets like API keys and access tokens are stored securely, regularly rotated, and closely monitored.
HYPR’s Identity Assurance platform combines phishing-resistant MFA, automated identity verification and real-time identity risk mitigation to combat today’s threats as well as those to come. It’s built to fit seamlessly into your current identity stack, whether that’s Microsoft Entra ID or another provider. To learn more, arrange a demo tailored to your environment and use cases.
Baljeet Sandhu
CTO
Baljeet Sandhu is the Chief Technology Officer at HYPR, where he leads the engineering behind its secure, passwordless authentication solutions. With over 20 years of experience in cybersecurity and software engineering, he has held senior roles at Barclays, Bank of America, and RBC. His expertise spans cryptography, cloud architecture, and API development, all essential to HYPR’s mission of building trusted identity systems.
Related Content

