Stay ahead of the curve with the latest news, ideas and resources on all things Identity Assurance and Passwordless.
Best Practices for Identity Proofing in the Workplace
Highlights:
- What is identity proofing and why it's crucial to protect against employee fraud
- Which verification methods are traditionally used in the workforce - A breakdown of the NIST identity proofing guidelines
- How to create a strategy based on best practices that addresses critical moments in the identity life cycle



With employee identity risk and fraud on the rise — to the point that the FBI has issued a public warning — it’s crucial to ensure that employees are who they say they are. Is the person you interviewed the same person you actually hired? Is the person logging in a legitimate employee? Is the person requesting a credential reset in fact the owner of those credentials? Robust identity proofing helps you answer those questions.
Understanding Identity Proofing and Why It’s Needed
What is identity proofing? Identity proofing is the process of verifying and validating the identity of individuals accessing digital systems. It ensures that the identity exists and that the person claiming the identity is the real owner. Employee identity proofing is a fundamental aspect of safeguarding sensitive information, intellectual property and overall organizational integrity. It addresses one of the major security weaknesses in most IAM systems — the fact that authentication only validates that the credentials being used to access systems are valid. It cannot ensure that the person using those credentials is the legitimate holder, and further that the legitimate holder is actually who they claim to be.
Workplace Identity Fraud Escalating
The rise of remote work and the increase in attacks on identity processes underscore the critical need for reliable methods of verifying and validating employee identities. Using credentials obtained by brute force attacks, phishing, AitM attacks, social engineering and other methods, cybercriminals can readily gain unauthorized access to systems and networks. Sometimes the attacks aren’t particularly sophisticated, but exploit gaps in verification processes to perpetrate identity fraud.
Consider the case of the attack on MGM resorts. Armed with publicly available details, attackers impersonated an employee and convinced the IT help desk to provide them with credential access to the corporate IAM service. From there they could wreak havoc, stealing sensitive data and deploying ransomware that shut down operations for over a week.
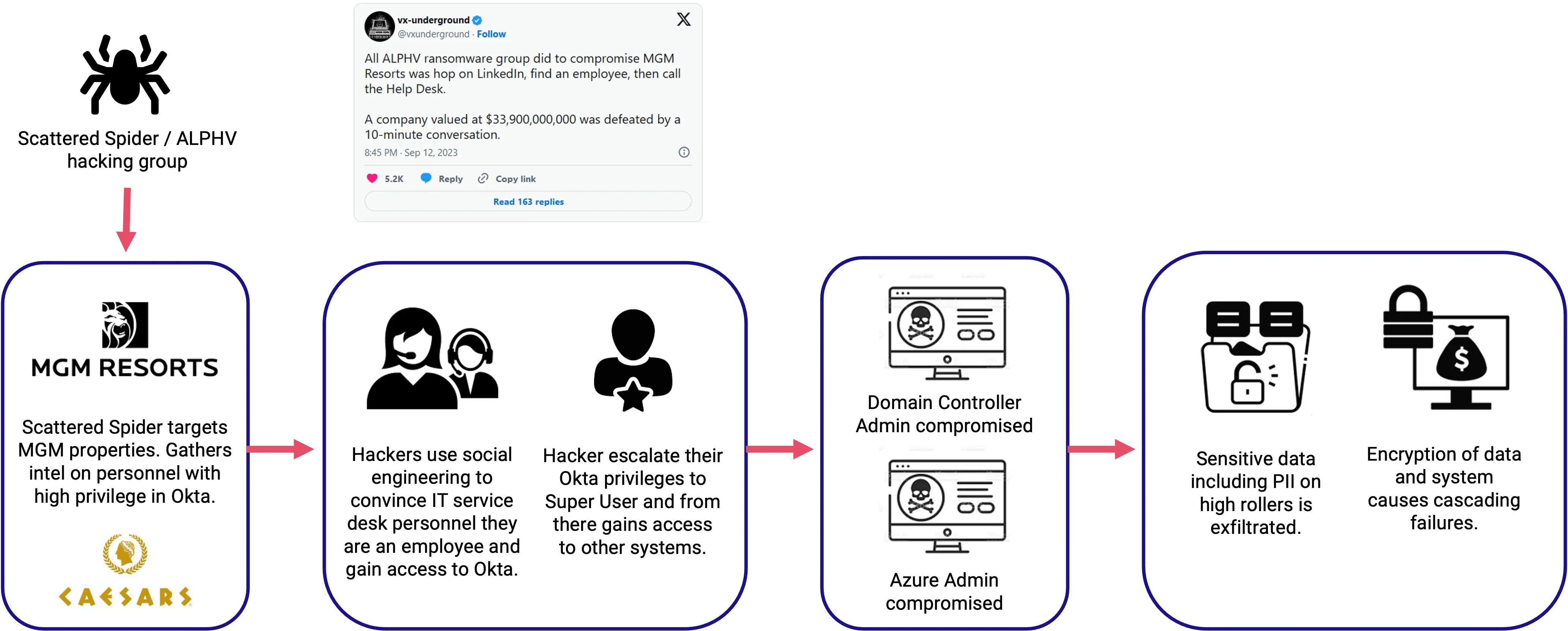
MGM Resorts attack flow
By implementing stringent identity proofing and know your employee protocols, organizations can ensure regulatory compliance and mitigate the risk of unauthorized access, data breaches, and other malicious activities.
Key Components of Identity Proofing for the Workforce
Worker identity proofing should include multiple verification methods to increase the security of the proofing process. The methods used will depend on the situation and context. Ideally all components are connected both to each other and to your other workforce access security tools and systems.
Document Verification
Document verification determines whether a document — such as a passport, driver’s license or other official document — is authentic or not. This can be done either in person or digitally. Your document verification process should include technology that is able to detect forgeries or alterations.
Location Detection
Location detection is an important aspect of online identity proofing. Is the employee in the geolocation you expect them to be? If not, this may require further investigation. It’s important, however, that your location detection adheres to global regulations.
Facial Recognition With Liveness Detection
Facial recognition uses facial biometrics to determine if a person matches the identity they are claiming. Usually the person will take a selfie as part of the identity proofing process. Liveness detection is a critical feature when using facial verification in order to detect spoofing tactics such as a photo, video playback or even a mask.
Live Video Verification
Live video verification adds an additional layer of security to the identity proofing process. It takes place face-to-face over a video conference, between the employee and their supervisor or an authorized agent and includes questions and actions designed to confirm liveness and detect signs of spoofing or coercion.
Chat Verification
In some cases, such as a lower risk scenario, chat verification may be sufficient. It also may be used as part of a more comprehensive identity proofing flow. Effective chat verification combines AI and human interaction.
Attestation
Attestation by a responsible party of the identity proofing results is a critical part of the process. This creates an official trail for audit and compliance purposes. Your identity proofing software should retain the attested results, not the employee’s sensitive data.
The integration of these diverse methods creates a comprehensive identity proofing ecosystem, enhancing cybersecurity measures and safeguarding organizations from unauthorized access and data breaches.
NIST Identity Proofing Guidelines
Identity proofing holds a critical role in IAM. Under the National Institute of Standards and Technology (NIST) Digital Identity Guidelines, NIST SP 800-63-A covers enrollment and identity proofing. It outlines a general identity proofing flow and describes three different security levels based on the strength of the type of evidence gathered as well as the verification processes used.
Identity Assurance Level 1 (IAL1): This level does not require the user to be linked to a known, established real-life identity. It uses self-asserted attributes — in other words, no identity proofing.
Identity Assurance Level 2 (IAL2): IAL2 introduces the requirement for strong proof connecting the user to a valid, real-world identity. It supports a wide range of identity proofing methods, allowing for either remote or in-person validation. This includes government-issued documentation as well as biometrics; proofing cannot rely on knowledge-based techniques.
Identity Assurance Level 3 (IAL3): IAL3 is the strictest identity proofing level, requiring user presence and biometric verification.
Best Practices for Effective Workforce Identity Proofing
Many companies verify a worker’s identity at the time of hire and stop there. Make sure your identity proofing strategy addresses all key workplace scenarios and times of increased risk of fraud. Below are some of the most critical moments to address.
Employee Onboarding
Before giving any new hire access to corporate systems and data, HR teams need to ensure that the person they are onboarding has a credible identity and is the legitimate owner of the identity they are claiming. They also need to verify that the new employee is in fact the person that was interviewed for the role. This means elements of identity proofing need to come into play before a candidate steps a real or virtual foot into the office. It’s also crucial to securely tie the new employee’s verified identity to IAM systems using non-phishable methods.
Credential Resets
In many organizations, identity proofing stops at HR’s door. The newly minted employee is provisioned with a digital identity and from that point on verification involves validation of that digital identity — there is no process for ensuring it ties back to the real world holder of that identity. This leaves them vulnerable to social engineering attacks that target the credential reset process. For example, an attacker with the right information can claim to be an employee with a new phone that needs to enroll in MFA on their new device.
Changing Roles
A change in roles often provides an employee with access to systems previously out of reach. Before granting those elevated privileges, organizations should make sure that the role change is legitimate and the user is who they claim to be.
Elevated Detected Risk
When identity monitoring systems detect potential risks, re-proofing may be indicated depending on the risk level and threat type. For example, if a user attempts to log in from a device that is not in proximity to their computer or engages in other suspicious activity, they could be automatically prompted to provide proof that they are the valid credential holder.
HYPR: Revolutionizing Workplace Identity Verification
HYPR Affirm is a comprehensive identity verification solution designed for large and complex organizations. It’s the first solution tailored to meet the unique needs of workforce employee identity proofing throughout the full employee lifecycle.
HYPR Affirm leverages AI-powered chat, video, face recognition and other cutting-edge technologies to create a seamless, secure and fully passwordless method of confirming employee identities. It provides IAL2 compliance and supports step-up re-proofing of identity based on user behavior or risk.
The best way to learn about HYPR's employee identity proofing solution is to see it in action. Contact us to arrange a demo, tailored to your identity security interests and needs.
FAQs
Q: What is identity proofing and why is it important?
A: Identity proofing is the process of verifying and validating the identity of an individual. It is important to ensure that individuals accessing systems or services are who they claim to be, preventing fraud, unauthorized access, and protecting sensitive information.
Q: What are the key components of an effective identity proofing process?
A: An effective identity proofing process includes document verification, biometric authentication, liveness detection, behavioral analytics and other verification methods. Combining these elements enhances the accuracy and security of the identity verification process.
Q: How is identity proofing applied in different industries?
A: Identity proofing is widely applied across industries such as finance, healthcare, e-commerce, and government. In finance, it helps prevent fraudulent transactions; in healthcare, it safeguards patient data; in e-commerce, it secures online transactions, and in government, it ensures secure access to sensitive information.
Q: How does HYPR's identity verification solution work?
A: HYPR's identity verification solution, HYPR Affirm, utilizes a range of identity proofing and verification technologies, such as advanced biometrics and liveness detection, to guarantee that only authorized individuals can access corporate systems and data.
Q: Can identity proofing prevent unauthorized access effectively?
A: Identity proofing plays a crucial role in preventing unauthorized access when combined with other identity security elements. Integrating identity proofing with phishing-resistant passwordless authentication and continuous identity risk monitoring, to create a complete identity security solution, makes it significantly more difficult for unauthorized individuals to gain access to systems, accounts, or sensitive information.
Joshua Gonzales
Senior Product Marketing Manager
Joshua Gonzales is a Senior Product Marketing Manager at HYPR, where he helps position the company’s authentication solutions in the identity security space. He previously led go-to-market strategies at cybersecurity companies such as Beyond Identity, and also worked as a social media consultant for major brands including HarperCollins and Express. Joshua’s background in cybersecurity and digital storytelling helps convey the importance of eliminating passwords and building trust in the identity lifecycle.
Related Content

