Stay ahead of the curve with the latest news, ideas and resources on all things Identity Assurance and Passwordless.
Toward Converged Identity Assurance: An Analyst Perspective



Identity and access management (IAM) is a crucial security component and a business enabler for the modern enterprise — but it’s clear that current systems are falling short on both fronts. Enterprises remain rife with legacy systems, technology silos, and manual and disconnected processes that were never intended to cope with today’s complex identity environment. New threat vectors, often aided by generative AI, exploit the gaps in this patchwork of systems, with increasingly alarming consequences.
A robust identity security strategy requires the consolidation of a broad set of identity assurance capabilities into a unified approach. A new position paper by industry analyst Simon Moffatt of the Cyber Hut explores the current state of IAM security and proposes guidelines for organizations to build a comprehensive Identity Assurance approach that can tackle these challenges.
Key Findings
Enterprises Face Multiple Operational and Identity Security Challenges
The current technological landscape has become increasingly complex, characterized by hybrid deployments, fragmented technology silos, and inadequate visibility and metrics. Employee onboarding and credential management processes remain manual and disjointed, creating friction and security gaps. The rising volume and variety of remote work and people supply chains puts further strain on systems and business.
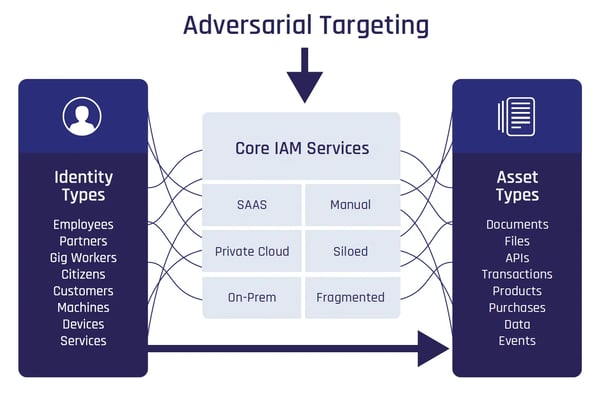
Outdated Authentication and Identity Verification Processes Prevalent
Authentication stands out as a critical pinch point in user interactions, presenting both opportunities and challenges. Many organizations employ multiple MFA solutions without a clear pathway to consolidation or adoption of phishing-resistant passwordless authentication.
Moreover, the lack of coherence and continuity in identity verification and validation processes severely impacts business and security, leading to issues such as cumbersome employee verification, fraud, credential theft, account takeover, and data breaches.
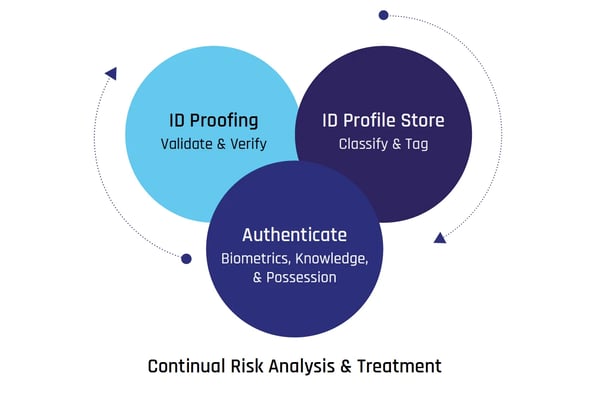
The Need for Converged Identity Assurance
A comprehensive Identity Assurance strategy involves viewing authentication in stages of maturity, moving from siloed and coarse-grained methods to relying on an assured identity that is continually verified. The goal is to reduce fragmentation and trust boundaries, and overlay existing authentication with verified identities on an ongoing basis.
By embracing a converged Identity Assurance approach, organizations improve identity security, accelerate adoption of Zero Trust principles, improve IAM productivity, and reduce their compliance exposure.
More Findings and Recommendations
You can read the full analyst white paper here, including a detailed mapping of the identity lifecycle, how to identify your own security gaps and a capability analysis for building your Identity Assurance strategy.
Learn how HYPR's comprehensive Identity Assurance solution helps you secure the entire identity lifecycle.
Joshua Gonzales
Senior Product Marketing Manager
Joshua Gonzales is a Senior Product Marketing Manager at HYPR, where he helps position the company’s authentication solutions in the identity security space. He previously led go-to-market strategies at cybersecurity companies such as Beyond Identity, and also worked as a social media consultant for major brands including HarperCollins and Express. Joshua’s background in cybersecurity and digital storytelling helps convey the importance of eliminating passwords and building trust in the identity lifecycle.
Related Content
