Stay ahead of the curve with the latest news, ideas and resources on all things Identity Assurance and Passwordless.
The AI Forgery Epidemic: The Growing Threat of AI-Generated Fake Documents


As CEO of HYPR, I spend a lot of time thinking about the future of identity security. And right now, one of the most significant shifts we're witnessing is driven by the rapid advancement of Artificial Intelligence. While AI offers incredible potential, it also presents formidable challenges, particularly in the realm of identity verification. The uncomfortable truth is that the era of relying solely on scanning a driver's license or passport to prove someone is who they claim to be is rapidly coming to an end. AI has made forging these documents disturbingly easy, rendering traditional methods dangerously inadequate.
How Advanced AI Undermines Traditional Document Checks
We've all seen the headlines about generative AI tools like GPT-4o, Midjourney, and others. Their ability to create text, images, and even video from simple prompts is astounding. Unfortunately, this power extends to creating highly convincing counterfeit identity documents. What once required specialized skills, equipment, and significant time can now be achieved by malicious actors in mere minutes.
This isn't a theoretical future threat; it's happening now. The implications for businesses relying on Know Your Customer (KYC) and employee identity verification processes are immense. From financial institutions onboarding new clients to travel companies verifying passengers, the foundational assumption that a presented document is genuine is crumbling under the weight of AI-driven forgery. This ease of access to sophisticated forgery tools democratizes identity fraud on an unprecedented scale, posing a severe risk to businesses and consumers alike.
How AI Like GPT-4o Can Effortlessly Create Convincing Fake Passports and IDs
The alarming reality of AI's forgery capabilities was starkly demonstrated recently in a widely shared post on LinkedIn by Borys Musielak. He highlighted just how simple and accessible this threat has become.
As Borys shared, using generative AI capabilities available in models like GPT-4o, it took him a mere five minutes to create a convincing digital replica of his own passport. This wasn't a theoretical exercise; it was a practical demonstration yielding a fake document that, in his assessment, would likely sail through many automated KYC systems currently in use without raising any red flags.
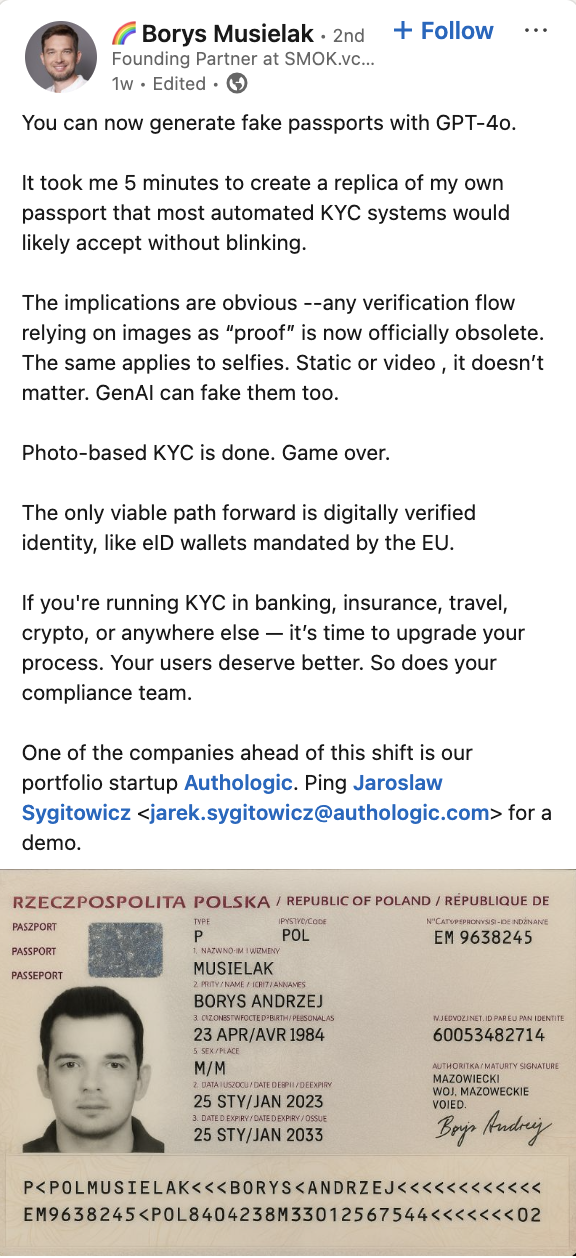
Borys's conclusion was blunt and accurate: "Photo-based KYC is done. Game over." And he's absolutely right. He further noted, "any verification flow relying on images as 'proof' is now officially obsolete. The same applies to selfies. Static or video, it doesn’t matter. GenAI can fake them too."
This isn't about spotting blurry, amateurish fakes anymore. We're talking about high-resolution images possessing all the visual hallmarks of genuine documents, generated with frightening speed and ease. To the untrained human eye, and critically, to many legacy automated verification systems, these fakes are virtually indistinguishable from the real thing. These systems, often designed to spot layout inconsistencies or basic digital manipulations, are simply not equipped to detect pixel-perfect forgeries created by AI trained on vast datasets of real documents.
The types of foundational documents now easily counterfeited digitally include:
- Passports: Essential for international travel and high-value transactions.
- Driver's Licenses: Widely used for domestic identification, age verification, and accessing services.
- National ID Cards: Key for government services, voting, and proof of citizenship in many countries.
- Birth Certificates: Often the root document used to obtain other forms of identification.
Why Relying Only On Document-Based ID Verification Is an Outdated Approach
The consequence of this AI-powered forgery capability is stark: traditional, document-centric identity verification is becoming obsolete as a standalone method. Relying solely on a submitted image of an ID, or even pairing it with a selfie (which can also be faked using deepfake technology), is no longer a sufficient security measure.
Why is this the case?
- Perfect Replication: AI can analyze thousands of genuine documents and learn to replicate their structure, fonts, layouts, and subtle visual elements with near-perfect accuracy.
- Beyond Static Images: The threat isn't limited to document images. AI can generate fake selfies ("deepfakes") and even manipulate video feeds in real-time, fooling liveness checks that require a user to blink or turn their head.
- Ease of Bypass: Fraudsters armed with these AI-generated fakes can easily circumvent onboarding processes, open fraudulent accounts, launder money, and commit other serious crimes, leaving businesses liable and customers vulnerable.
Continuing down the path of document-only verification is like putting a padlock on a screen door. It looks like security, but it provides no real protection against a determined adversary armed with modern tools. Businesses clinging to these outdated methods are not just failing to stop fraud; they are actively exposing themselves and their legitimate customers to significant financial and reputational risk.
Multi-Factor Identity Verification: The Necessary Path Forward
So, if documents alone are no longer reliable, what's the answer? The solution lies in a multi-layered, multi-factor approach to identity verification. Instead of relying on a single, forgeable piece of evidence, we must validate multiple, independent factors simultaneously during a single user interaction.
Think of it like securing a high-value facility. You wouldn't rely solely on a single keycard; you'd incorporate security guards, cameras, biometric scans, and access logs. Similarly, robust identity verification requires multiple signals triangulated together to build confidence in the user's identity. This dramatically increases the complexity and cost for fraudsters, making it exponentially harder to bypass checks using only a fake document.
Key Components of Secure Multi-Factor Verification
A truly secure multi-factor identity verification process doesn't just ask for more things; it intelligently combines different types of signals. At HYPR, we believe the essential components include:
- User's Device Trust: Is the user interacting from a device (phone, computer) that is known and trusted? Analyzing device integrity, reputation, and security posture provides a critical anchor. Leveraging technologies like passkeys, which bind the user to the device cryptographically, adds a powerful layer.
- Location & Network Context: Does the user's location (derived from IP address, GPS, network signals) align with expected patterns? Is the network connection suspicious (e.g., coming from a known VPN or proxy associated with fraud)? Contextual data provides vital clues.
- Advanced ID Document Validation (As One Factor, Not the Only Factor): We remotely analyze submitted document photos using sophisticated digital forensics to detect forgery and cross-reference key information against trusted national databases.
- Simultaneous Validation & Orchestration: Crucially, these factors must be checked together in a single, orchestrated session. A fraudster might be able to spoof one factor (like location via a VPN) or possess a fake document, but faking a trusted device, a plausible location, and passing advanced document checks all at the same time is significantly more challenging.
Benefits of Multi-Factor Approach Over Document-Only Verification
Adopting a modern, multi-factor verification strategy delivers tangible advantages:
- Dramatically Reduced Fraud: Makes it exponentially harder for fraudsters to succeed with only fake documents.
- Layered Security: Creates multiple barriers; if one factor is compromised, others still stand guard.
- Enhanced Compliance: Helps meet evolving regulatory requirements that increasingly recognize the limitations of document-only checks.
- Improved User Experience: Modern solutions can orchestrate these checks seamlessly in the background, often requiring less active user participation than more cumbersome processes.
- Increased Trust: Demonstrates a commitment to highest security, reassuring users that their identities are being properly protected.
The Inevitable Path to Verified Digital Identities
Multi-factor verification is the crucial defense against current threats. But the long-term solution involves moving beyond verifying static documents altogether and embracing verified digital identities.
Think of a physical wallet containing your driver's license, credit cards, and health insurance card. A digital identity wallet securely stores verified, cryptographically signed digital credentials on your smartphone or device. When you need to prove your identity online, you present the relevant digital credential from your wallet, which can be verified instantly and securely without transmitting unnecessary personal data.
Flaws in Traditional KYC Processes Across Industries
The reliance on outdated, document-centric KYC is a systemic vulnerability affecting numerous sectors:
- Banking & Finance: Exposure to account opening fraud, money laundering, and regulatory fines.
- Insurance: Fraudulent claims, policy inception fraud based on fake identities.
- Travel & Hospitality: Circumvention of watchlists, booking fraud, non-compliance with passenger verification mandates.
- Cryptocurrency Exchanges: High susceptibility to money laundering and sanctioned individuals using fake IDs.
- Gig Economy & Marketplaces: Platform abuse, background check evasion, trust and safety issues.
- Government Services: Benefits fraud, unauthorized access to citizen services.
In all these areas, the risks of clinging to document-only verification are clear: rampant fraud, regulatory penalties, operational inefficiencies dealing with fraud fallout, and perhaps most damagingly, the erosion of customer trust.
Digitally-Verified Identity: The Necessary Evolution of KYC
The future of secure and user-friendly KYC lies in verified digital identity. Forward-thinking governments and regulatory bodies, like the EU with its eIDAS 2.0 framework and digital identity wallets, are already paving the way. This approach offers a paradigm shift:
- Cryptographically Secure: Identity data is bound to the user and verified using strong cryptography, making forgery virtually impossible.
- Verifiable Credentials: Users present specific, verified attributes (like "is over 18" or "is a resident of X state") without revealing underlying sensitive data.
- Interoperable Standards: Built on common standards ensuring compatibility across different services and jurisdictions (e.g., eIDAS, GDPR principles of data minimization).
- User Control & Privacy: Users control their own identity data within their digital wallets.
- Seamless Experience: Enables secure, passwordless authentication and instant identity verification, creating a frictionless user journey.
Choosing the Right Digital Identity Verification Partner
Transitioning to a modern identity verification strategy requires the right technology partner. As you evaluate solutions, consider these key aspects:
- Multi-Factor Verification: Does the platform incorporate device trust, location context, behavioral signals, and advanced document checks with sophisticated orchestration? Does it have proven fraud detection capabilities against modern threats?
- Seamless User Experience: How easy is the verification process for legitimate users? Does it work across web and mobile, and for various use cases (onboarding, login, transaction verification)?
- Compliance & Standards: Does the solution support relevant regulations (e.g., GDPR, CCPA) and emerging digital identity standards?
- Integration & Flexibility: How easily can the platform integrate with your existing technology stack (via APIs, SDKs)? Can it adapt to your specific risk policies and workflows?
- Future-Proofing: Does the provider demonstrate a commitment to innovation and staying ahead of evolving threats like AI-driven fraud?
Stay Ahead of Fraudsters with Multi-Factor, Digital Identity Verification
The security landscape is shifting beneath our feet. AI-powered tools have democratized sophisticated identity fraud, making traditional document verification methods dangerously inadequate. Waiting to act is no longer an option
By embracing a multi-factor identity verification strategy, incorporating signals like device trust and location context alongside advanced document checks, businesses can build immediate, robust defenses. Looking ahead, the transition to verified digital identities offers a path to even greater security, privacy, and user convenience.
At HYPR, we are committed to providing the solutions organizations need to navigate this complex environment. Protecting your business and your customers from identity fraud in the age of AI isn't just good practice; it's an imperative for building and maintaining trust.
Ready to modernize your identity verification process and safeguard your organization against AI-driven threats?
Subscribe to our updates to receive expert insights and learn how HYPR's multi-factor verification and digital identity solutions can protect your business and customers.
Bojan Simic
CEO, HYPR
Bojan Simic is the Chief Executive Officer & Co-Founder of HYPR. Bojan's vision for the elimination of shared secrets and his experience in authentication & cryptography serves as the underlying foundation for HYPR technology and company strategy. Previously, he served as an information security consultant for Fortune 500 enterprises in the financial and insurance verticals conducting security architecture reviews, threat modeling, and penetration testing. Bojan has a passion for deploying applied cryptography implementations across security-critical software in both the public and private sectors. Bojan also serves as HYPR’s delegate to the FIDO Alliance board of directors, empowering the alliance’s mission to rid the world of passwords.
Related Content


